Description du réseau :
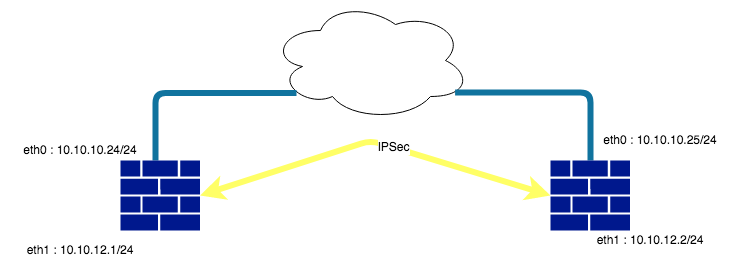
Préparation du routeur :
nano /etc/sysctl.conf
net.ipv4.ip_forward = 1
net.ipv6.conf.all.forwarding = 1
net.ipv4.conf.all.accept_redirects = 0
net.ipv4.conf.all.send_redirects = 0sysctl -p
Installation du service IPSec avec StrongSwan
apt-get update
apt-get install strongswanSRV1
nano /etc/ipsec.conf
config setup
charondebug="all"
uniqueids=yes
conn ipsec1-to-ipsec2
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
left=10.10.10.24
leftsubnet=10.10.12.1/24
right=10.10.10.25
rightsubnet=10.10.13.1/24
ike=aes256-sha1-modp1024!
esp=aes256-sha1!
aggressive=no
keyingtries=%forever
ikelifetime=28800s
lifetime=3600s
dpddelay=30s
dpdtimeout=120s
dpdaction=restartnano /etc/ipsec.secrets
10.10.10.24 10.10.10.25 : PSK "SYmm+7box2OzHt3q5bJl5K3c/6sBS28l"SRV2
nano /etc/ipsec.conf
config setup
charondebug="all"
uniqueids=yes
conn ipsec2-to-ipsec1
type=tunnel
auto=start
keyexchange=ikev2
authby=secret
left=10.10.10.25
leftsubnet=10.10.13.1/24
right=10.10.10.24
rightsubnet=10.10.12.1/24
ike=aes256-sha1-modp1024!
esp=aes256-sha1!
aggressive=no
keyingtries=%forever
ikelifetime=28800s
lifetime=3600s
dpddelay=30s
dpdtimeout=120s
dpdaction=restartnano /etc/ipsec.secrets
10.10.10.25 10.10.10.24 : PSK "SYmm+7box2OzHt3q5bJl5K3c/6sBS28l"Commande utile :
ipsec restart : redemarrer la connexion
ipsec status : état du service et route montée